If you have newly embarked on an email authentication journey and have configured only SPF for your emails, chances are your emails might not be reaching all your clients. When you are a part of a large MNC or enterprise, you must be sending out marketing emails to all your customers, and partners on a daily basis using mailing lists or via email forwarding. If that is the case, this might be one of the potential pitfalls and a major contributing factor to your emails not being delivered if you have SPF enabled. Let’s find out why.
Regular Email Vs Email Forwarding?
The difference between regular emailing and forwarded emails lies in the path that the email takes.
Let’s consider a scenario wherein two email servers are communicating with each other over a regular email transfer. In this case, the email message is directly sent from the sending server to the receiver server and it takes a simple, unidirectional, and linear route.
Now, let’s consider a scenario where an email is being sent by the domain owner using mailing lists. In this case, the email goes through at least one intermediary server before it reaches the receiving server. There is no direct communication between the sending and receiving servers.
The problem with SPF and Forwarding
Sender Policy Framework (SPF) is an email authentication standard that allows you to keep a list of all authorized IP addresses that can send emails on behalf of your domain or from your domain in your DNS. This list is kept in the form of a TXT record that needs to be updated from time to time as you use more and more third-party email vendors.
The following is an example of a simple SPF record:
v=spf1 ip4:155.155.155.155 -all
This means that only emails that are being sent from the server with an IP address of 155.155.155.155 will pass SPF authentication on the receiver’s side. However, since during email forwarding the email passes through an intermediary server, which, albeit, has a different IP address (every email server has a unique IP), this leads to SPF authentication failure. Most forwarded emails almost always fail SPF which makes it imperative to keep additional measures in place so as to ensure that legitimate emails never fail to be delivered.
How can DKIM help?
While SPF relies on the return-path information present in the email header, DKIM works by affixing a unique cryptic value to the message body. Since the contents of an email remain unchanged during email transfer even when it is a forwarded message, the DKIM key is preserved through the transfer. This allows the receiving server to match this key against the public key in the sender’s DNS during authentication. When a match is found, the email gets delivered.
Hence email forwarding has no impact on the DKIM authentication results if the email is coming from an authentic source, barring a few exceptions and special cases. This highlights the importance of publishing a DKIM record for your domain along with SPF to improve your deliverability.
Monitor your Authentication Results with DMARC
If you have DMARC enabled for your domain, you would want to achieve DMARC compliance on your emails. Configuring SPF alone will result in DMARC failure if your emails are DKIM neutral. This is why the first step towards achieving compliance would be to set up a DKIM record for your domain.
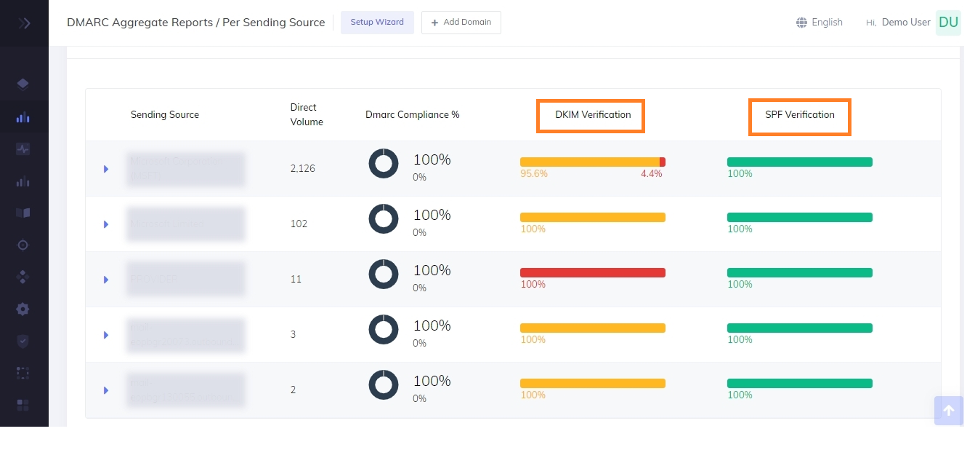
Another important step towards a safer email experience is to enable DMARC monitoring. Our DMARC report analyzer helps you view your SPF and DKIM authentication results in detail so you can track failed deliveries due to email forwarding, and fix the problem faster. Given below is a screenshot of the PowerDMARC dashboard to show you how convenient it is to monitor your email’s performance on our portal:
Create a DMARC record today to steer clear of fake emails and impersonation attempts on your domain!







